5 min read
Why You Need to Start Threat Hunting Within Your Network
 Andy Oesterheld
:
Apr 16, 2024 3:15:00 AM
Andy Oesterheld
:
Apr 16, 2024 3:15:00 AM

Written by Andrew Oesterheld and Todd Welfelt
Almost every successful cyberattack on an organization leaves some form of network-level footprint. It may be access logs on a firewall, unusual access activity from an end user's workstation, or file transfers to an unexpected location.
Each activity goes through the network, but you must capture and analyze all network traffic within your organization to ensure these activities are noticed.
This is different from firewall logs and network flow data, which is unfortunately insufficient.
Firewalls only log what they are programmed to alert on, which can be anywhere from the occasional alert to an avalanche of connection logs that provide no real value. The Firewall logs themselves range from vague to robust. LAN flow data is too high-level and fails the capture the details of the actual payload in the packets, which is required for finding threats within the network
Using the network data to identify suspicious activity increases your ability to identify an attack before it's too late.
In this article, we will discuss two major reasons to implement network monitoring and threat hunting in your organization:
Reason #1: Proactive Threat Detection
 Threat actors' capabilities to evade defenses are advancing at an alarming pace. This trajectory we've observed as a community has continued in the last decade.
Threat actors' capabilities to evade defenses are advancing at an alarming pace. This trajectory we've observed as a community has continued in the last decade.
While advances in endpoint protection, such as EDR, have made protecting IT environments easier, many techniques can be used to completely evade endpoint sensors, from something as simple as using LOLBins (such as PowerShell and WMI) to creating customized malicious tooling that uses complex methods to evade EDR hooks.
While the most advanced actors might be able to pass through endpoint defenses, they still must communicate over the network, which is their ultimate bottleneck.
They can only make so many moves, and with a properly monitored, baselined, and segmented network, it can become much easier to find "invisible" threats.
For example, most actors will use RDP (Remote Desktop Protocol) to move laterally across the network. With proper network monitoring, we can easily see anomalous RDP sessions that can call out this activity. Often, actors will perform this activity from VPN networks or during off-hours for the organization. They use it excessively, creating visible spikes in the network traffic that stick out like sore thumbs.
.png?width=194&height=115&name=image%20(46).png)
Fig. 1: RDP Traffic Spike on PacketWatch platform
Network Visibility Using the PacketWatch Platform
 Our tool, PacketWatch, allows organizations to gain proper visibility into their network traffic. We use advanced network parsers and detections to identify threats proactively.
Our tool, PacketWatch, allows organizations to gain proper visibility into their network traffic. We use advanced network parsers and detections to identify threats proactively.
Often, when we disclose threats or suspicious activity we have identified in our hunts, there are no EDR or endpoint alerts. Only the network traffic reveals what is hiding in the endpoint.
Threat Detection Example: How PacketWatch Network Monitoring Foiled an Initial Access Broker
An excellent example of this was a recent incident we detected and remediated.
On January 1, 2024, we discovered evidence of what was most likely an Initial Access Broker (IAB) trying to gain persistence in one of our client's networks.
Despite this client utilizing one of the top three EDR solutions currently available, due to not fully deploying the solution and the actor using tools such as Impacket (which often does not generate EDR alerts if used carefully), this EDR solution did not generate any alerts for the actor's malicious activity.
However, our tool detected the anomalous traffic as potential Impacket activity, and further threat hunting discovered more evidence of the actor's attempts at brute forcing and running exploits in a desperate move to attain some persistence. As they attempted persistence, we alerted our client and led them through the successful remediation of this incident.
More details of this incident can be found here.
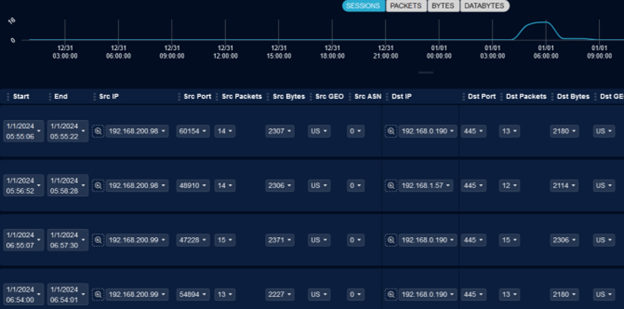
Fig. 3: Impacket activity spike as seen on PacketWatch platform
The Problem with Relying on Next-Generation Anti-Virus (NGAV) Solutions
Using advanced next-generation anti-virus solutions that analyze behaviors on protected endpoints significantly reduces risk over traditional file-based solutions. But these agents can't be deployed everywhere, and the threat actors know this.
Tactics are evolving to target systems that typically lack protection, such as IoT devices, DVRs, printers, and other ancillary systems.
While the amount of data available on these is minimal compared to workstations or servers, a threat actor can capture network packets, decrypt transmissions, and gain authorized credentials for the environment. Using authorized credentials, the threat actor has almost unlimited access to an environment, and the advanced anti-virus solution does not notice anything unusual.
The Key to Network Monitoring: Baselining Your Environment
Like hardware-level monitoring, the key to network-level monitoring lies in understanding what is normal and expected within an environment and what diverges from the baseline.
Using guidance from sources on the typical Tactics, Techniques, and Procedures (TTPs) can help focus efforts on specific types of traffic, protocols, and applications within an organization.
Reason #2: Regulatory Recommendations
![]() NIST has recently published its Cyber Security Framework update (CSF 2.0), an overhaul designed to address modern cybersecurity challenges.
NIST has recently published its Cyber Security Framework update (CSF 2.0), an overhaul designed to address modern cybersecurity challenges.
While adherence to the framework is largely voluntary, some companies require the CSF for their customers or within their supply chain. You can learn more about NIST-CSF 2.0's major updates here.
This update introduces new categories in the Detect Function and Continuous Monitoring Category (DE.CM).
The five recommendations are to monitor and find potentially adverse effects in the following areas:
- Networks and Network Services
- Physical Environment
- Personnel Activity and Technology Usage
- External Service Provider Activities
- Computing Hardware and Software
Of these five items, four can be identified through network activity monitoring, and of those four, three can best be detected through monitoring of network activity against established baselines.
Government Guidance Example: LOTL Techniques
On February 7, 2024, the Department of Defense released guidance on detecting and monitoring malicious activity that discusses leveraging network monitoring to identify additional signs of malicious behavior and to limit lateral movement associated with an attack in Section 3.
The government guidance focused on mitigating Living Off The Land (LOTL) techniques recently published to the public. The report was published in light of recently disclosed threat actor activity, particularly around threat actors sponsored by the People's Republic of China (PRC) and their ability to evade most defenses and gain access to nations' critical infrastructure.
One of the four "hardening best-practices" listed in this guidance was "Enhance IT and OT network segmentation and monitoring."
On page 17, they go into more detail:
"Enhance network segmentation and monitoring to limit lateral movement possibilities for threat actors. Abnormal network behavior may indicate the presence of a threat actor that evaded host-based detections, possibly via LOTL techniques. Properly implementing and managing network segmentation ensures that users only have access to the minimum number of applications and services to perform their daily duties. When a cyber threat actor compromises legitimate credentials, having appropriate network segmentation limits the "blast radius" of accessible systems.
- Use network traffic analysis tools to monitor inter-segment traffic, focusing on unusual patterns or communications to sensitive segments.
- Strategically place network sensors and network traffic parsers at critical points in the network infrastructure, such as intersections between different network segments, external gateways/virtual private networks (VPNs), and demilitarized zones (DMZs). Ensure these sensors have deep packet inspection capabilities to facilitate comprehensive traffic analysis.
- Employ network traffic metadata parsers (e.g., Zeek, [formerly Bro]) for efficient parsing and analysis of network traffic, enabling the identification of suspicious patterns and anomalies indicative of LOTL activities. Also, consider integrating open-source network intrusion detection systems (NIDS) (e.g., Snort, Suricata) to improve LOTL threat detection."
We at PacketWatch have seen first-hand the need for network monitoring and threat hunting. Most organizations do not even think to do this or do so only with the intention of monitoring system issues.
Conclusion
An organization's security plan must include network monitoring and active threat hunting as critical components. Network monitoring and threat hunting can enhance and support existing traditional protections, like endpoint anti-virus, by identifying actions and activities that these traditional methods may miss.
Organizations need proper network visibility and the ability to access real-time and historical network data and the metadata related to those events to avoid exposing themselves to an increasing number of threat actors that evade modern EDR and other endpoint-focused protection systems.
This is not a new trend in cybersecurity but rather a continuation of the traditional layered approach to security, which involves overlapping methods of detection and coverage.
Network visibility is so important that NIST, CIS, NSA, and others advise network monitoring as an additional protection against malicious activity.
We at PacketWatch have created a tool over several years and are ready to help organizations achieve full network visibility through our PacketWatch network monitoring tool.
Our clients receive proper visibility into their network and are monitored by some of the industry's best and most experienced threat hunters.
If any incident occurs, our hunters are proven and able to guide your organization quickly and effectively through remediation. Threat hunting's proactive nature not only detects threats before they cause damage but also hunts for vulnerabilities and misconfigurations that can be resolved before a malicious actor exploits them.
Contact us today to see our software in action and meet our talented team.
DISCLAIMER
Kindly be advised that the information contained in this article is presented with no final evaluation and should be considered raw data. The sole purpose of this information is to provide situational awareness based on the currently available knowledge. We recommend exercising caution and conducting further research as necessary before making any decisions based on this information.


.png?width=429&height=225&name=IAB%20PacketWatch%20Network%20Monitoring%20(1).png)