Enterprise Security Assessment (ESA)
An Enterprise Security Assessment can give you a holistic view of your IT and Security environments.
Get Panoramic Views of Your Network
Uncover Your Risks
Don't wait for vulnerabilities to become exploits. Schedule your Enterprise Security Assessment with our team.
Contact Us
Ready to get started?
We're here to help. Reach out to schedule an introductory call with one of our team members to learn how PacketWatch can benefit your organization and bolster your security operations.
Measuring Your Security Posture
How do you know if your cybersecurity policies, procedures, and controls are effectively protecting your organization?
An Enterprise Security Assessment (ESA) will give you a comprehensive view of your IT and Security environments. Combining multiple assessment methodologies, our cybersecurity experts will show you where your defenses are strong, where there are gaps, and provide a roadmap toward improvement.
Within a month, you’ll know more about your network than you thought possible.
Comprehensive Assessment Coverage
Network Security
Cloud + Email Security
Identity Security
Threats + Vulnerabilities
Framework Review
Benefits of an ESA
- Determines if your current security defenses are protecting your organization
- Scores controls, practices, and procedures using a security framework for your industry
- Identifies vulnerabilities and tests them to see if your controls mitigate the risk
- Scours your network for advanced persistent threats and anomalous behaviors
- Monitors your network for a complete business cycle to uncover abnormal activities
The purpose of an Enterprise Security Assessment is to give you an accurate and comprehensive understanding of your organization’s security and risk posture. Through this process, we’ll analyze your threat landscape, look at internal and external vulnerabilities, monitor your network, and scan threat intelligence and Dark Web data to look at your organization from an adversary’s perspective.
We’ll uncover risks that other tools and teams may have missed. This assessment’s holistic and comprehensive nature is what makes it a powerful tool for IT, security, and business executives.
Our experts will show your team everything that we find and how they can avoid, accept, mitigate, or transfer the risk. We’ll also deliver a formal report and an executive presentation.
Enterprise Security Assessment Steps and Timeline
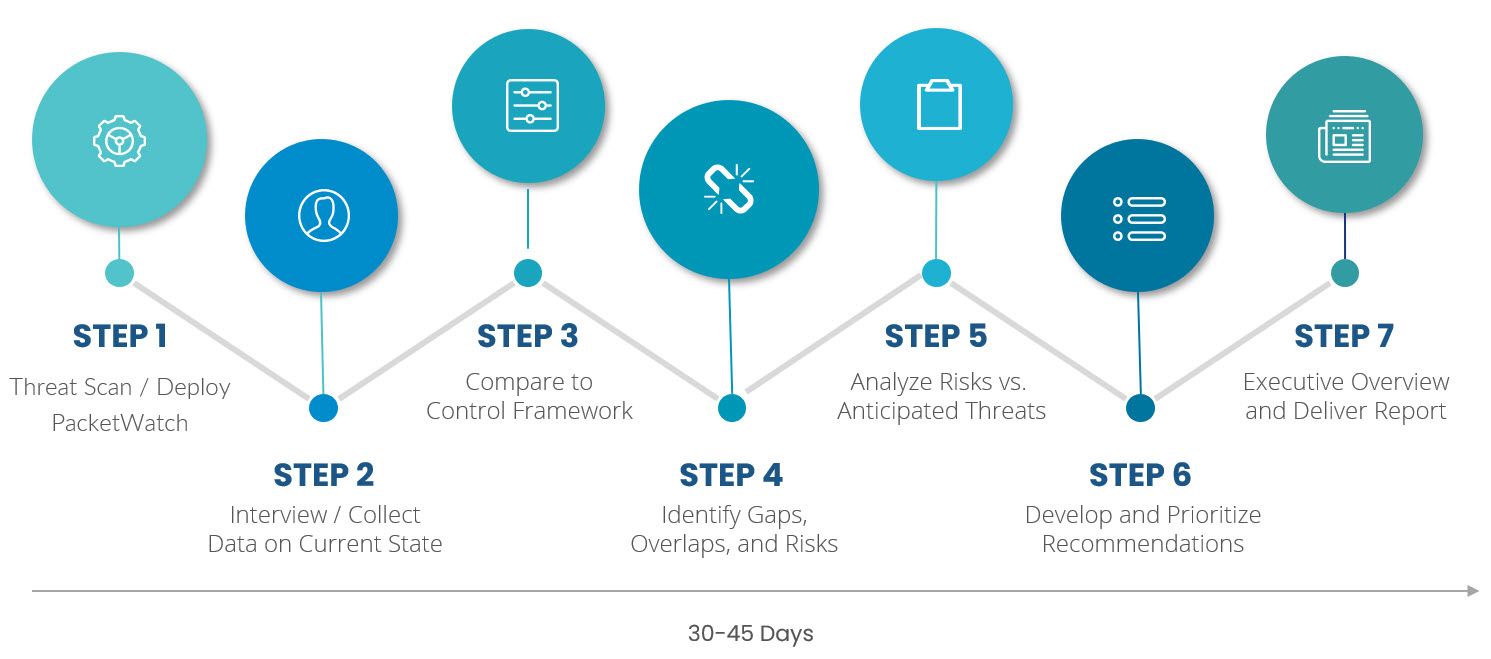
Methodology
The PacketWatch ESA compiles a variety of cybersecurity perspectives, including direct observations, interviews, controls evaluations, scans, and a comparison to the most appropriate security framework.
The assessment collects network data over a complete business cycle to capture any persistent network activities and anomalies that may occur sporadically over time.
Scope
This comprehensive evaluation of your network, endpoints, servers, email, cloud services, identity management, web applications, storage, backups, and power management will look at configurations, best practices, warranty status, security posture, maturity, resiliency, and survivability.
Our experts will analyze your threat landscape and assess your policies, procedures, and controls.
Technology
The assessment uses our PacketWatch platform along with proven industry-standard scanning, penetration testing, and endpoint detection and response tools to collect and analyze your data.
The proprietary toolset uses packet-level data to uncover malicious activity, expose misconfigured devices, identify vulnerable assets, reveal policy violations, and detect persistent anomalous events.
We Understand Industry-Specific Compliance and Regulation
How your organization mitigates risk and complies with federal, state and local regulations is unique to your business, industry, and technology environment.
PacketWatch understands the unique needs of highly regulated industries like Healthcare, FinTech, Government Contractors, Manufacturing, Elections, and more.
Leverage a Mature Team of Cybersecurity Experts
Our cybersecurity team possesses vast experience in federal law enforcement, national security agencies, global enterprises, and regulated industries, making them highly skilled threat investigators.
They have an acute awareness of what to search for, including patterns, anomalies, and potential blind spots that less experienced analysts may overlook.
They understand digital forensics to meticulously investigate threats, avoid false positives, and provide detailed reports with practical recommendations for remediation.

.png?width=4000&height=2800&name=Desktop_Dashboard%20(1).png)
Powered by the PacketWatch Platform
PacketWatch is an expert threat hunting platform that delivers network monitoring, analysis, and investigation platform.
The platform incorporates full-packet-capture network monitoring, multiple intrusion detection systems (IDS), several threat intelligence feeds, big data analytics, high-speed search, and robust machine learning to detect known and unknown threats and provide total network visibility.

