Digital Forensics and Incident Response (DFIR)
PacketWatch helps organizations respond to security incidents caused by all forms of attack, such as malware, ransomware, or business email compromise.
Experiencing a Cyber Attack?
Get Immediate Assistance
We are available 24/7 for potential and existing clients experiencing a cyber incident.
Call our Incident Response Hotline at 1-800-864-4667 and press 9 for Priority Assistance.

Your Trusted Incident Response Team
Make PacketWatch your first call when you have an attack or incident.
Our experienced Digital Forensics and Incident Response (DFIR) experts are on standby, ready to provide immediate assistance. Unlike other firms, we don't believe in the "escalation model" of service where customers are stuck on the line as they shuffle calls through Tier 1 to Tier 3 responders.
Our IR Team is composed of only battle-hardened, experienced analysts who are ready to handle your incident the moment you call.
Respond
Our IR experts engage your team immediately.
We get straight to work--triaging, investigating and remediating the incident. We introduce experts from the beginning of the project remain involved and lead the entire engagement.
Resolve
Our Incident Response team works collaboratively with your team to remediate the issue and highlight any other suspicious activity on your network.
PacketWatch has extensive experience documenting, collecting, and preserving evidence for legal and internal reference.
Report
Once the incident has been contained, we work to document digital forensics and generate a thorough report.
We also provide strategic security recommendations to avoid future incidents.
Reinforce
Once your incident has been resolved, we provide 30 days of additional monitoring with additional updates from a dedicated analyst.
We assist with recovery and additional services to strengthen your organization's security posture and long-term operations.
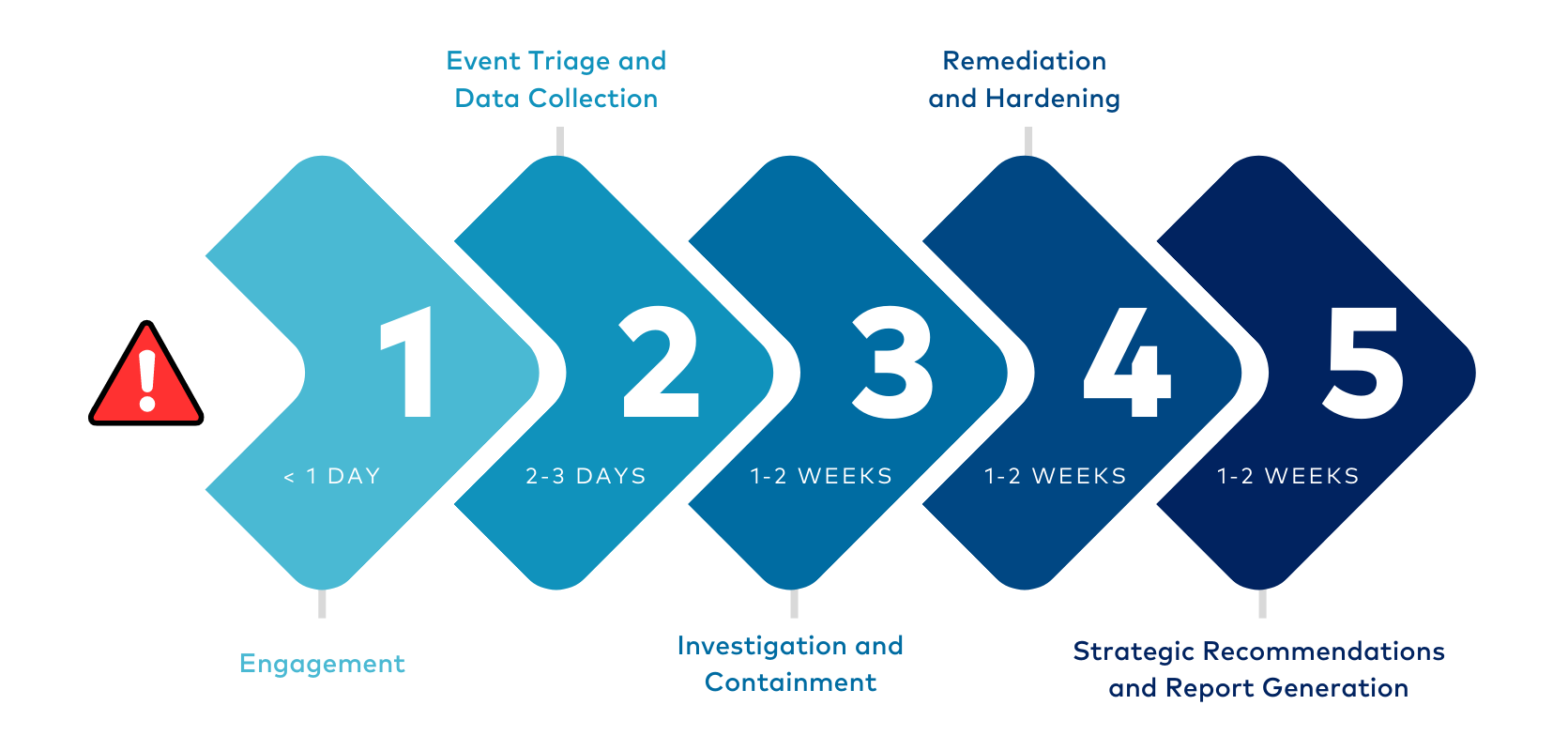
Our DFIR Approach
PacketWatch rapidly deploys world-class tools and technology to ensure threats can no longer operate unnoticed—the goal is more visibility than you’ve ever seen before. We actively partner with our clients to identify and eliminate any threats. Our collaborative incident response methodology shares the “hows” and “whys” along the way to develop the clients’ cybersecurity skills and capabilities.
Responsive Expertise
PacketWatch helps organizations respond to security incidents caused by all forms of attack, such as malware, ransomware, or business email compromise. Our team consists of threat hunters, investigators, threat intelligence analysts, forensic analysts, and cybersecurity experts with experience in federal law enforcement, military, national security, local law enforcement, and large enterprises.
Our team engages quickly and gets right to work—triaging, investigating, and remediating the incident. As a boutique consultancy, the experts we introduce at the beginning of the project remain involved and lead the entire engagement. Our clients can also leverage our extended team of forensic specialists, data scientists, cyber insurance professionals, intelligence experts, and cyber-focused legal experts.
The Human Element
A security incident is an unsettling time. Stakeholders want to know that everything is going to be okay. But that often involves several crucial steps, collaboration with experts, and time. We believe there is a human element to cybersecurity. So, we work with our clients shoulder-to-shoulder—leading them through the incident and teaching them how to strengthen their defenses. The result is an IT team and infrastructure that is better prepared for a future attack. Our security experts also help the client’s executive team regain confidence in their systems, processes, policies, and people.
Effective Cyber Incident Response Performed by Elite Experts
We are on standby, ready to provide immediate relief.


