Digital Forensics and Incident Response (DFIR)
PacketWatch helps organizations respond to security incidents caused by all forms of attack, such as malware, ransomware, or business email compromise.
Experiencing a Cyber Attack?
Get Immediate Assistance
We are available 24/7 for potential and existing clients experiencing a cyber incident.
Call our Incident Response Hotline at 1-800-864-4667 and press 9 for Priority Assistance.

Your Trusted Incident Response Team
Make PacketWatch your first call when you have an attack or incident.
Our experienced Digital Forensics and Incident Response (DFIR) experts are on standby, ready to provide immediate assistance. Unlike other firms, we don't believe in the "escalation model" of service where customers are stuck on the line as they shuffle calls through Tier 1 to Tier 3 responders.
Our IR Team is composed of only battle-hardened, experienced analysts who are ready to handle your incident the moment you call.
Respond
Our IR experts engage your team immediately.
We get straight to work--triaging, investigating and remediating the incident. We introduce experts from the beginning of the project remain involved and lead the entire engagement.
Resolve
Our Incident Response team works collaboratively with your team to remediate the issue and highlight any other suspicious activity on your network.
PacketWatch has extensive experience documenting, collecting, and preserving evidence for legal and internal reference.
Report
Once the incident has been contained, we work to document digital forensics and generate a thorough report.
We also provide strategic security recommendations to avoid future incidents.
Reinforce
Once your incident has been resolved, we provide 30 days of additional monitoring with additional updates from a dedicated analyst.
We assist with recovery and additional services to strengthen your organization's security posture and long-term operations.
Our DFIR Approach
PacketWatch rapidly deploys world-class tools and technology to ensure threats can no longer operate unnoticed—the goal is more visibility than you’ve ever seen before. We actively partner with our clients to identify and eliminate any threats. Our collaborative incident response methodology shares the “hows” and “whys” along the way to develop the clients’ cybersecurity skills and capabilities.
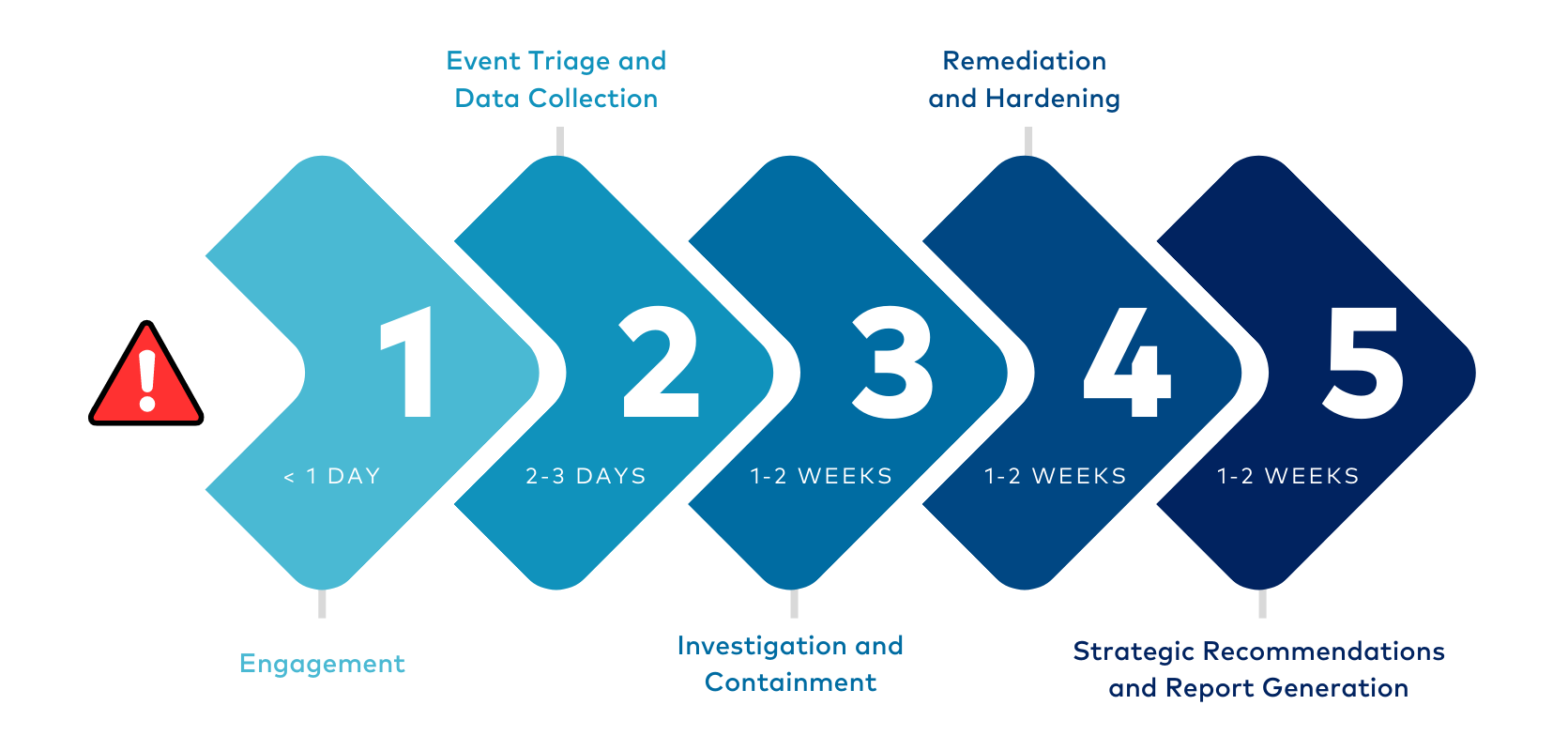
Responsive Expertise
PacketWatch helps organizations respond to security incidents caused by all forms of attack, such as malware, ransomware, or business email compromise. Our team consists of threat hunters, investigators, threat intelligence analysts, forensic analysts, and cybersecurity experts with experience in federal law enforcement, military, national security, local law enforcement, and large enterprises.
Our team engages quickly and gets right to work—triaging, investigating, and remediating the incident. As a boutique consultancy, the experts we introduce at the beginning of the project remain involved and lead the entire engagement. Our clients can also leverage our extended team of forensic specialists, data scientists, cyber insurance professionals, intelligence experts, and cyber-focused legal experts.
The Human Element
A security incident is an unsettling time. Stakeholders want to know that everything is going to be okay. But that often involves several crucial steps, collaboration with experts, and time. We believe there is a human element to cybersecurity. So, we work with our clients shoulder-to-shoulder—leading them through the incident and teaching them how to strengthen their defenses. The result is an IT team and infrastructure that is better prepared for a future attack. Our security experts also help the client’s executive team regain confidence in their systems, processes, policies, and people.
Effective Cyber Incident Response Performed by Elite Experts
We are on standby, ready to provide immediate relief.
Digital Forensics and Incident Response (DFIR) Service Providers
Most organizations realize they must be able to quickly respond to cybersecurity incidents, such as ransomware or other cyber attacks, but do not have the resources to do so.
There are a number of Digital Forensics and Incident Response (DFIR) firms that have popped up within the last year.
PacketWatch has been providing DFIR services for years, working alongside in-house security teams, legal parties, compliance experts, and insurance firms.
Increasingly, Cyber Insurance firms require organizations to have an Incident Response retainer agreement in place to lower costs and manage the risk of their portfolios.
Gartner Definition
Gartner broadly defines DFIR services as the digital forensic examination and investigation capabilities to analyze digital channels, memory, social media, cloud services, endpoint systems, devices, and applications.
The objective is to identify fraud and/or malicious, unethical, or illegal activities and threat actors (internal or external).
For an investigation to take place, an activity with malicious intent (such as a breach) is suspected or detected at an organization. The DFIR investigators must endure that any evidence is collected following proper procedures, conduct a thorough examination, establish a chain of custody for evidence collection, and prepare for potential legal proceedings.
Most incident response plans use some variation of the process as described in the National Institutes of Standards and Technology's (NIST) SP 800-61 Rev. 2.
Incident Response Considerations
According to NIST's Computer Security Incident Handling Guide, there are a few ways to structure and staff your IR team:
Team Structure
-
Internal Employees: The organization performs all of its incident response work with limited technical and administrative support from contractors.
-
Partially Outsourced: The organization outsources portions of its incident response work. Although incident response duties can be divided among the organization and one or more outsourcers in many
ways, a few arrangements have become commonplace:
-
The most prevalent arrangement is for the organization to outsource 24-hours-a-day, 7-days-a-week (24/7) monitoring of intrusion detection sensors, firewalls, and other security devices to an offsite managed security services provider (MSSP). The MSSP identifies and analyzes suspicious activity and reports each detected incident to the organization’s incident response team.
-
Some organizations perform basic incident response work in-house and call on contractors to assist with handling incidents, particularly those that are more serious or widespread.
-
-
Fully Outsourced: The organization completely outsources its incident response work, typically to an onsite contractor. This model is most likely to be used when the organization needs a full-time, onsite incident response team but does not have enough available, qualified employees. It is assumed that the organization will have employees supervising and overseeing the outsourcer’s work.
Cost
Organizations may fail to include incident response-specific costs in budgets, such as sufficient funding for training and maintaining skills. Because the incident response team works with so many facets of IT, its members need much broader knowledge than most IT staff members.
Staff Expertise
Incident handling requires specialized knowledge and experience in several technical areas; the breadth and depth of knowledge required varies based on the severity of the organization’s risks. Outsourcers may possess deeper knowledge of intrusion detection, forensics, vulnerabilities, exploits, and other aspects of security than employees of the organization. Also, MSSPs may be able to correlate events among customers so that they can identify new threats more quickly than any individual customer could.
Employee Morale
Incident response work is very stressful, as are the on-call responsibilities of most team members. Many organizations will also struggle to find willing, available, experienced, and properly skilled people to participate, particularly in 24-hour support.
The Need for 24/7 Availability
Real-time availability is the best for incident response because the longer an incident lasts, the more potential there is for damage and loss.
Full-Time Versus Part-Time Team Internal Members
Organizations with limited funding, staffing, or incident response needs may have only part-time incident response team members, serving as more of a virtual incident response team. In this case, the incident response team can be thought of as a "volunteer fire department."
Incident Response Process
-
Preparation
Companies need a plan to both prevent and respond to events. -
Detection and Analysis
Once detected, organizations must determine whether an incident occurred, its severity, and its type. -
Containment, Eradication, and Recovery
IR teams must work together to contain the threat from doing any more damage to their environment.
Next, they must eradicate the threat. Eradication may include actions such as deleting malware, disabling breached user accounts, and identifying and mitigating all exploited vulnerabilities.
Lastly, in recovery, administrators restore systems to normal operation, confirm that the systems are functioning normally, and remediate vulnerabilities to prevent similar incidents. -
Post-Incident Activity
Last, IR teams focus on learning and improving. The organization should reflect on new threats, where to improve technology and lessons learned.
Mandatory Reporting of Cyber Incidents
One area of reporting that U.S. companies should be aware of is the recent Cyber Incident Reporting for Critical Infrastructure Act of 2022 (CIRCIA).
While covered cyber incident and ransomware payment reporting under CIRCIA will not be required until the Final Rule implementing CIRCIA’s reporting requirements goes into effect, CISA encourages critical infrastructure owners and operators to voluntarily share with CISA information on cyber incidents prior to the effective date of the final rule.
Organizations designated as “covered entities” by CISA will be subject to the cyber incident and ransomware reporting provisions in CIRCIA. A covered entity could include companies or organizations within a critical infrastructure sector such as commercial facilities, communications, critical manufacturing, emergency services, energy, financial services, food and agriculture, government facilities, healthcare and public health, and information technology.
Failing to Report to CISA under CIRCIA
According to Bryan Cave Leighton Paisner's analysis of CIRCIA:
"If a covered entity fails to report a covered cyber incident or ransom payment, CISA may issue a request for information to the covered entity. If the covered entity fails to respond or to respond adequately to CISA’s information request within 72 hours, CISA may issue a subpoena to compel disclosure. If the covered entity fails to comply with the subpoena, CISA may refer the matter to the Attorney General, who may bring a civil action to enforce the subpoena; failure to comply with the subpoena may be punishable by contempt. Once again, however, specific procedures for carrying out these enforcement provisions and 'other available enforcement mechanisms' will be developed during the rulemaking process."
Resources
- Market Guide for Digital Forensics and Incident Response Services (Gartner)
- Guide for Cybersecurity Event Recovery (NIST)
- Incident Response Plan (IRP) Basics (CISA)
- Ransomware Guide (CISA)
- Incident Command System (ICS) Advisory Project - Dashboard
Digital Forensics and Incident Response (DFIR) Statistics
0%
of initial access was through phishing¹
$0
average ransomware payment in 2020²
0
seconds that an organization will experience a cyber attack³
Sources: ¹The DFIR Report, ²Icoinical, ³Icoinical



