Security Risk Analysis (SRA)
Organizations under the HIPAA Security Rule are required to complete a Security Risk Analysis annually to remain compliant. Trust PacketWatch's team of information security experts to thoroughly assess your environment.

Security Risk Analysis Performed by Compliance and Information Security Experts
Data breaches and regulatory enforcement actions continue to rise, implementing and sustaining a Health Insurance Portability Accountability Act (HIPAA) compliance program adherent to the Security, Privacy, and Breach Rules is critical to avoid severe consequences, including civil and criminal penalties.
PacketWatch's Security Risk Analysis service gives your organization a comprehensive snapshot of your current compliance with the HIPAA requirements and ongoing support to help you reach your compliance goals.

Risk Management Platform
Senior Compliance Team
Actionable Roadmap
Security Risk Analysis Overview
PacketWatch has the compliance and security expertise to meet your organization's needs. Our advisory team will help ensure your organization is compliant with the provisions and requirements of the Health Insurance Portability Accountability Act (HIPPA).
Our team takes the complexity of HIPAA requirements and breaks them into digestible pieces to help organizations remain compliant and help you prevent negative financial, operational, and reputational impacts from HIPAA violations.
Our experienced team will guide you through a detailed security risk analysis (SRA), meeting the federal requirements outlined in the Security Rule. The assessment identifies and ensures the implementation of proper safeguards to remain compliant with the standards and implementation specifications in the Security, Privacy, and Breach Notification Rules found in NIST 800-66.
The results of the SRA will identify how well the organization is complying with administrative, physical, and technical safeguards of the requirements.
PacketWatch SRA Process and Timeline
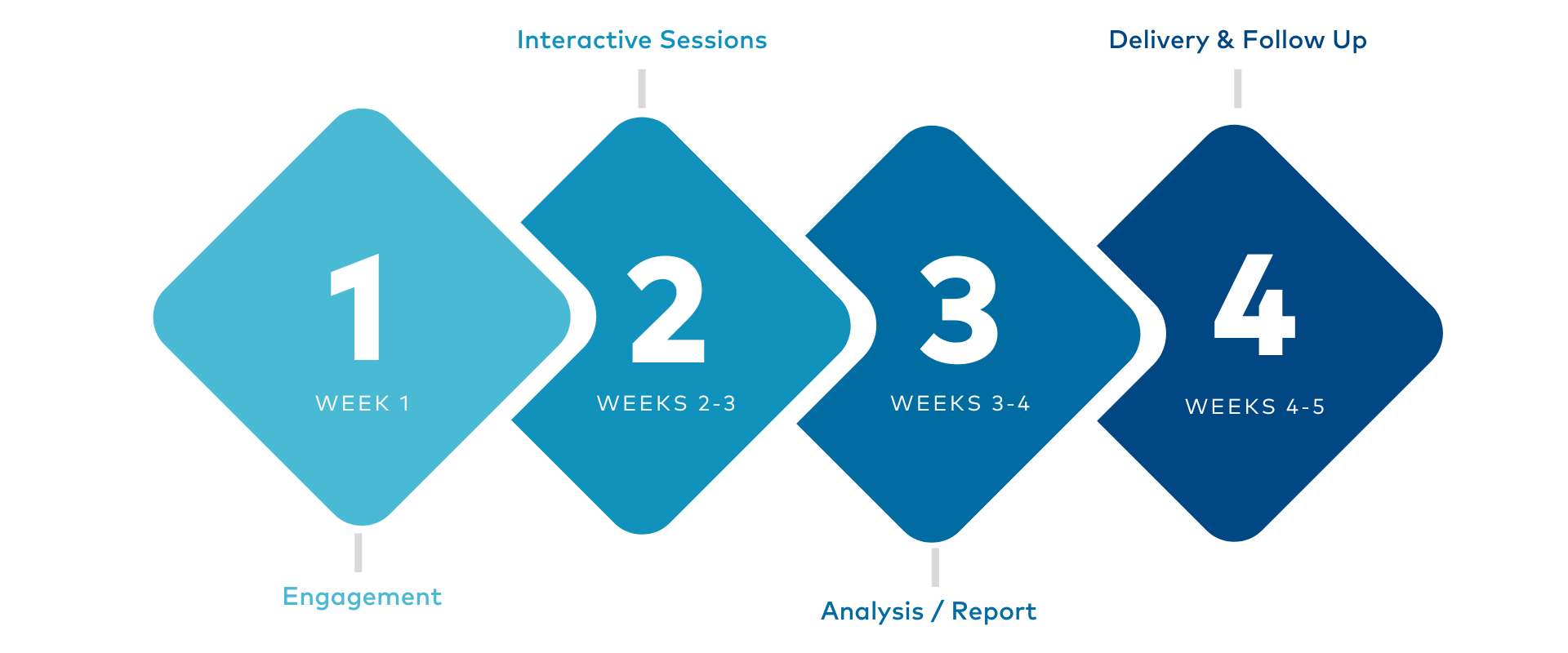
- Identify assets that create, receive, maintain, or transmit Electronic Protected Health Information (ePHI)
- Facilitate workshops and interviews with designated individuals within your organization to understand your company's current practices to identify risks and vulnerabilities
- Analyze collected data and materials to create an actionable roadmap for your organization to track progress in addressing gaps during the assessment
- Deliver a detailed report of findings with prioritized strategic and tactical recommendations for improvement
- Deliver an executive presentation to a non-technical audience of the results, findings, and roadmap
- Provide continuing access to PacketWatch's regulatory risk assessment and management platform to track progress
PacketWatch R2AM Platform
We conduct our guided analysis utilizing PacketWatch's proprietary Regulatory Risk Assessment Management (R2AM) platform to collect information and documentation through open discussions with individuals who are designated as the organization's subject matter experts (SMEs).
After completion of the SRA, we provide access to the R2AM platform for 12 months track your progress, establish milestones, consolidate documentation, provide evidence, and help mature your HIPAA compliance program.
Clients have access to their compliance results, may add documentation as it is developed and set reminders for upcoming milestones and deadlines.
For more information on all the assessments we perform on the R2AM platform and how we can improve your overall security compliance, contact us.
Benefits of Conducting an SRA
- Understand the effectiveness of your existing HIPAA program
- Identify and reduce ePHI and cyber security risks within your organization
- Raise awareness for the executive level of your ePHI and cyber security challenges, program gaps, and related breach impact
- Prioritize ePHI and security investment and resources to meet your business objectives
Frequently Asked Questions
-
Is a Security Risk Analysis a requirement of the Security Rule?
The U.S. Department of Health and Human Services (HHS) states in: §164.308
(a) A covered entity or business associate must, in accordance with § 164.306:
(1)
(i) Standard: Security management process. Implement policies and procedures to prevent, detect, contain, and correct security violations.
(ii) Implementation specifications:
(A) Risk analysis (Required). Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity or business associate.
(B) Risk management (Required). Implement security measures sufficient to reduce risks and vulnerabilities to a reasonable and appropriate level to comply with §164.306(a)…
-
What is a Security Risk Analysis?
A Security Risk Analysis identifies and documents all potential risks to your organization’s ability to do business.
It is one of the best ways to understand your organization's risk for threats like data loss, cyberattacks, or unintentional disclosure.
-
What should I do after an SRA?
To ensure long-term success and sustainability with the completion of the SRA, our HIPAA advisory team can support you with the risk management requirement by:
-
Work with your compliance team to develop and implement required policies and procedures.
-
Create and facilitate training to help the organization follow HIPAA regulations, reduce non-compliance risk, and operate effectively.
-
Prepare your organization for healthcare accreditation examinations.
Conduct Business Associate compliance audits.
-
Complete onsite privacy gap assessments.
Use the PacketWatch platform to validate the technical effectiveness of specific security controls implemented.
-
Conduct Vulnerability Assessments to ensure the proper functioning of patch management and vulnerability management programs (especially those managed by third parties).
-
Perform Penetration Testing, Application
-
Testing and Secure Code Reviews to ensure detection and response capabilities are functioning properly and ensure that internally developed applications are secure
If you need help maturing your organization's HIPAA compliance, reach out to us today.
-



