
On October 3, Daniel Stenberg (@badger) announced a forthcoming patch for cURL (version 8.4.0) that will be released on October 11, which includes a fix for a still unknown "high severity CVE".
Due to the widespread usage of curl, this vulnerability has the potential to be a major security risk.
Organizations are strongly encouraged to begin identifying where curl is used within their environment so that patches can be applied in a timely manner once they are released.
PacketWatch's Andrew Oesterheld has created several queries that can be used across various platforms to help identify where cURL is used.
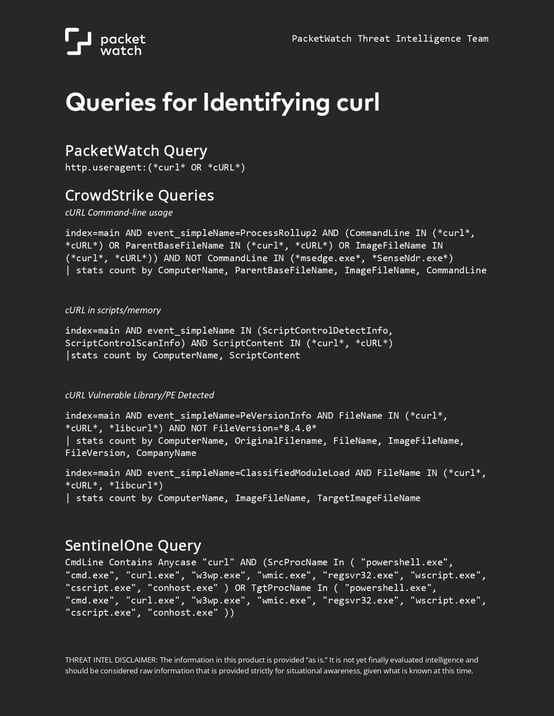
You can download a copy of the .pdf file by filling out the form below: