3 min read
Cyber Threat Intelligence Briefing - July 17, 2023
 The PacketWatch Intelligence Team
:
July 20, 2023
The PacketWatch Intelligence Team
:
July 20, 2023
.png)
Welcome back to another week of Cyber Threat Intelligence (CTI). This week's report highlights Russian hackers known as Storm-0978 and the new ways Microsoft Teams is being abused.
Russian Hackers Causing a Storm
Microsoft recently released a detailed blog highlighting a new phishing campaign from a Russian threat actor known as Storm-0978. This group is known for its deployment of a custom backdoor called 'RomCom', and has also been associated with a ransomware strain known as 'Underground'. This particular phishing campaign primarily targeted government and military organizations in Ukraine, as well as North American and European organizations involved in Ukrainian affairs. The key takeaway from this recent campaign is the exploitation of CVE-2023-36884 to deploy their RomCom backdoor.
What Is CVE-2023-36684?
Per Microsoft reporting, CVE-2023-36684 is a remote code execution vulnerability in Microsoft Windows and Office products. To exploit this vulnerability, the threat actor sends the user a specially crafted Office document, which the user needs to open, and then the malicious code embedded in the document executes in the context of the user's permissions.
At the time of this writing, exploit code for this vulnerability is not publicly available. However, due to the attention it has received, it is highly likely public proof-of-concept code will be disclosed in the coming days.
How To Protect Your Organization
This vulnerability does not currently have a patch available for remediation, effectively making it a 0-day. Per Microsoft, there are several steps that can be taken to mitigate attempted exploitation:
- Customers with Microsoft Defender for Office 365 are protected from attachments that attempt exploitation of this vulnerability.
- Microsoft Defender for Endpoint has a 'Block all Office applications from creating child processes' configuration capability. Enabling this feature has been shown to successfully block the exploitation of the vulnerability. Details for enabling this feature can be found here: Attack surface reduction rules reference | Microsoft Learn.
- Organizations that are not able to use the protections listed above can set the
FEATURE_BLOCK_CROSS_PROTOCOL_FILE_NAVIGATIONregistry key. It should be noted that setting this registry key could impact functionality and should be tested before deploying across the enterprise.
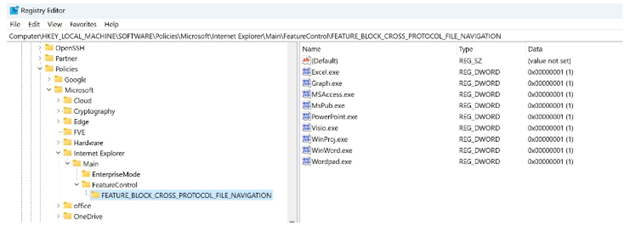
Fig. 1: Registry settings to prevent exploitation of CVE-2023-36884 (Microsoft.com)
Further recommendations for mitigating activity from Storm-0978 can be found in the 'Recommendations' section of the Microsoft Blog found here: Storm-0978 attacks reveal financial and espionage motives
Related Resources
New Ways to Abuse Microsoft Teams
Multiple tools and techniques have been disclosed recently showing novel ways of abusing Microsoft Teams to steal user credentials, facilitate session hijacking, and even deploy malware. Some of these techniques are also taking advantage of the Microsoft rebrand of Azure AD to Microsoft Entra ID.
The first example is a proof-of-concept video published by a researcher from security firm Cyvisory, known as 'pfiatde' on Twitter. In the demonstration, the attacker begins by sending a direct message to the victim over Microsoft Teams. This is accomplished due to the default Teams configuration that allows for tenants that reside outside of your organization to send messages to internal users. The phishing message then uses the pretext of the Microsoft rebranding to Entra ID to entice the user to click on a link to entra-id[.]cloud and enter their credentials. This site looks identical to a legitimate Microsoft Azure authentication portal. The phishing page harvests and forwards the user's credentials so they are authenticated to legitimate Microsoft services, while simultaneously the attacker gains session tokens allowing them to access the Azure portal under the context of the victim. It should be noted that multi-factor authentication (MFA) does not protect against this attack.
Next is a tool released last week called 'TeamsPhisher' published by a member of the U.S. Navy's red team. The tool takes advantage of the Microsoft Teams default configuration which allows for external tenants to send users a direct message. The command-line tool automates the process of validating the target has the correct (mis)configuration for the attack, creates a Sharepoint attachment link that hosts the malicious file, then sends the link in a new message thread to the victim.
How to Protect Your Organization
Microsoft is aware of the configuration issue that allows for these attacks, but issued a statement saying that since "it relies on social engineering to be successful" it does not meet the criteria for remediation. To prevent these attacks from reaching end users, organizations are strongly urged to disable communications with external tenants if it is not needed. If this is not able to be achieved, then users should be trained to be extra vigilant when interacting with messages from outside of their organization.
Related Resources
- https://devblogs.microsoft.com/identity/aad-rebrand/
- https://twitter.com/maikroservice/status/1679615314647224321
- https://www.bleepingcomputer.com/news/security/new-tool-exploits-microsoft-teams-bug-to-send-malware-to-users/
- https://www.bleepingcomputer.com/news/security/microsoft-teams-bug-allows-malware-delivery-from-external-accounts/
PacketWatch publishes this report and other cybersecurity threat intel to the security community for free via our blog. If you are interested in personalized threat intel, contact us today to learn about our enterprise threat intelligence services.
Disclaimer
Kindly be advised that the information contained in this article is presented with no final evaluation and should be considered raw data. The sole purpose of this information is to provide situational awareness based on the currently available knowledge. We recommend exercising caution and conducting further research as necessary before making any decisions based on this information.
