3 min read
Cyber Threat Intelligence Briefing - July 3, 2023
 The PacketWatch Intelligence Team
:
July 3, 2023
The PacketWatch Intelligence Team
:
July 3, 2023

Welcome back to another week of Cyber Threat Intelligence (CTI). This week's report highlights the use of QR codes in a new phishing campaign and guidance issued by the National Security Agency (NSA) to combat the BlackLotus malware.
QR Codes Used in New Phishing Campaign
Email security firm Inky published new research highlighting a phishing campaign leveraging multiple evasion techniques to bypass Email Gateways.
 The first notable evasion technique is the use of a photo image for the entire email body. There is no actual text in the email, only a picture showing the content of the email message.
The first notable evasion technique is the use of a photo image for the entire email body. There is no actual text in the email, only a picture showing the content of the email message.
Many email gateway filters look for text and string patterns within email content, but not image contents. Having all of the 'text' residing within an image bypasses these safety checks. The second evasion technique uses a QR code to obfuscate the malicious URL the user is directed to, hiding the link from the user and the email filters.
Other notable elements of this campaign include the impersonation of Microsoft support, urging the user to scan the QR code so that they can reset their credentials or add MFA to their account.
Additionally, the threat actor crafts the emails to appear as though they came from within the organization. The emails are worded in a way to instill a sense of urgency and fear, threatening users with account lockouts if they do not comply.
Once the user scans the QR code, they are directed to a fake Microsoft Authentication portal where the site will harvest the user's credentials.
How You Can Protect Your Organization
While the techniques leveraged by this campaign can bypass Email Gateway filters, there multiple detection and prevention opportunities:
- Users can inspect the sender's email address. Emails claiming to come from internal sources or Microsoft that do not actually come from those senders are immediate red flags.
- Train users to avoid scanning QR codes, especially ones sent via email. Ideally, users should be trained to never scan QR codes.
- Educate users to review the URL of any page where they are prompted to enter credentials. In this particular campaign, domains such as y7y[.]online were used for the Microsoft impersonation.
- Educate users to pay attention to browser warnings. In some cases, the browser can notify the user that the URL they are visiting is dangerous. These sites should be left immediately.
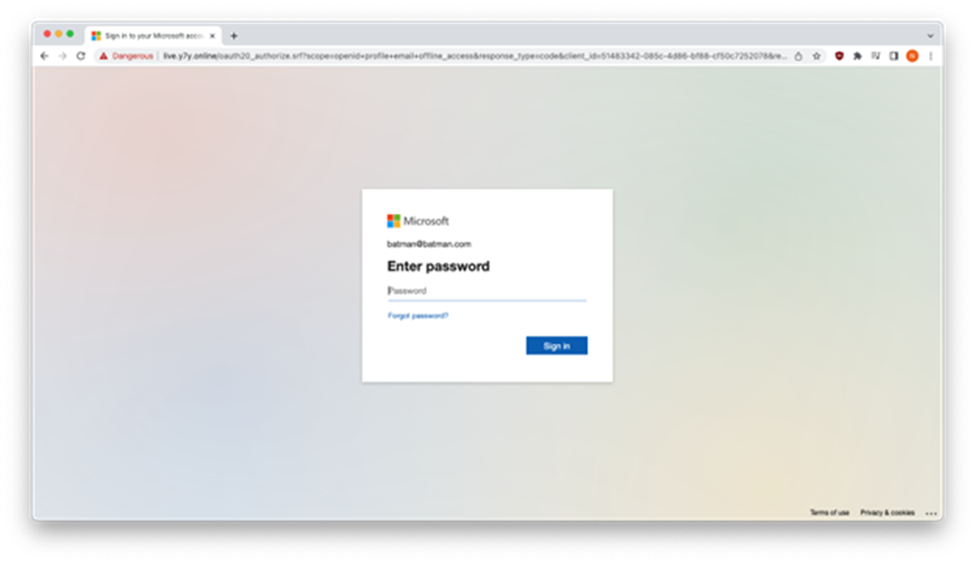
Figure 1: Fake Microsoft Authentication Portal (Source: Inky.com)
Related Resources
- https://www.inky.com/en/blog/fresh-phish-malicious-qr-codes-are-quickly-retrieving-employee-credentials
- https://arstechnica.com/security/2023/06/torrent-of-image-based-phishing-emails-are-harder-to-detect-and-more-convincing/
NSA Issues Guidance on Combatting BlackLotus Malware
The National Security Agency recently published detailed guidance for mitigating a new advanced malware called BlackLotus.
 This malware takes advantage of CVE-2022-21894, known as "Baton Drop", which is a boot loader flaw in Microsoft Windows. This allows the malware to take full control over an endpoint from the earliest phase of the software boot.
This malware takes advantage of CVE-2022-21894, known as "Baton Drop", which is a boot loader flaw in Microsoft Windows. This allows the malware to take full control over an endpoint from the earliest phase of the software boot.
While Microsoft issued patches to correct boot loader logic and help address the vulnerability, the NSA stresses that the patch is not sufficient as BlackLotus can still infect systems. This is due to the patch not revoking trust in unpatched boot loaders via the Secure Boot Deny List Database (DBX). Threat actors can substitute fully patched boot loaders with older vulnerable versions that will execute the BlackLotus malware.
There are several mitigation recommendations outlined by the NSA to detect and prevent BlackLotus:
-
Install the Microsoft patches from May 2023. Within this patch is an optional configuration to prevent rollback of the boot manager and kernel to versions vulnerable to BlackLotus. This is referred to as the "Code Integrity Boot Policy". Documentation for this step can be found here: KB5025885: How to manage the Windows Boot Manager revocations for Secure Boot changes associated with CVE-2023-24932 - Microsoft Support
-
The install process for BlackLotus malware involves multiple steps, including placing an older Windows boot loader binary into the boot partition, disabling of Memory Integrity, disabling of BitLocker, and a full reboot of the device. Modern EDR solutions can be configured to block one or more of these steps.
-
BlackLotus can be removed successfully if detected before the system reboots. Otherwise, a complete wipe of the infected host is required.
-
Modern EDR tools can also be configured to monitor the integrity of the boot partition. The NSA specifically recommends monitoring for changes to the 'bootmgfw.efi' and 'bootmgr.efi' files, as well as monitoring for unexpected Extensible Firmware Interface (EFI) binaries, such as 'shimx64.efi' or 'grubx64.efi'.
-
These mitigation techniques should also be applied to Windows virtual machines (VMs), as BlackLotus can also work in a virtual UEFI environment.
-
Additional "advanced" hardening techniques and further guidance can be found here: https://media.defense.gov/2023/Jun/22/2003245723/-1/-1/0/CSI_BlackLotus_Mitigation_Guide.PDF
Related Resources
- https://www.nsa.gov/Press-Room/Press-Releases-Statements/Press-Release-View/Article/3435305/nsa-releases-guide-to-mitigate-blacklotus-threat/
- https://insights.sei.cmu.edu/blog/uefi-terra-firma-for-attackers/
- https://thehackernews.com/2023/06/nsa-releases-guide-to-combat-powerful.html
PacketWatch publishes this report and other cybersecurity threat intel to the security community for free via our blog. If you are interested in personalized threat intel, contact us today to learn about our enterprise threat intelligence services.
Disclaimer
Kindly be advised that the information contained in this article is presented with no final evaluation and should be considered raw data. The sole purpose of this information is to provide situational awareness based on the currently available knowledge. We recommend exercising caution and conducting further research as necessary before making any decisions based on this information.
