6 min read
Cyber Threat Intelligence Briefing - January 29, 2024
 The PacketWatch Intelligence Team
:
January 29, 2024
The PacketWatch Intelligence Team
:
January 29, 2024

Welcome back for another bi-weekly threat intelligence report from PacketWatch. This week, we cover the VexTrio traffic broker, Kasseika BYOVD, and a vulnerability roundup.
VexTrio Traffic Distribution System

InfoBlox security researcher Christopher Kim, along with Randy McEoin, published a detailed report highlighting what is now the largest malicious traffic broker ever documented, known as VexTrio.
Their research was able to identify over 60 affiliates leveraging the VexTrio network, including ClearFake and SocGholish, notorious fake-update malware distributors.
VexTrio acts as a traffic distribution system (TDS), which redirects unsuspecting users to malicious pages based on a number of criteria such as operating system, geolocation, and more.
InfoBlox has been able to identify over 70,000 legitimate websites that have been compromised by VexTrio. These sites were found to be running vulnerable versions of content management systems such as WordPress and Joomla.
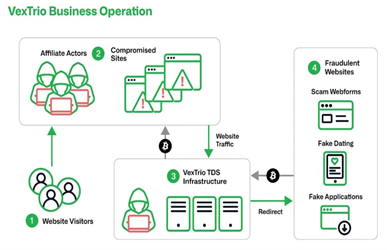
Fig. 1 – VexTrio ecosystem Source: InfoBlox
How To Protect Your Organization
Per InfoBlox, the following steps will help mitigate VexTrio and similar TDS networks:
- Limit web activity to secure websites that use a Secure Sockets Layer (SSL) certificate. A secure website’s URL should begin with “https” rather than plain “http.”
- Look for the green lock icon when visiting unfamiliar websites and click on the icon to review the website’s authenticity.
- Do not allow push notifications from untrusted websites.
- Consider using an adblocker program to block certain malware activated by popup ads. Along with an adblocker, consider using the web extension NoScript, which allows JavaScript and other potentially harmful content to execute only from trusted sites to reduce the attack surface available to actors.
Additionally, using a network monitoring device such as PacketWatch can enable defenders to identify malicious traffic from VexTrio via PacketWatch detections and manual threat hunting for suspicious web traffic. Finally, any identified malicious domains should be blocked at the external firewall. IOCs and PacketWatch hunting queries for VexTrio can be found here.
Additional Resources
- https://blogs.infoblox.com/cyber-threat-intelligence/cybercrime-central-vextrio-operates-massive-criminal-affiliate-program/
- https://thehackernews.com/2024/01/vextrio-uber-of-cybercrime-brokering.html
- https://www.bleepingcomputer.com/news/security/vextrio-tds-inside-a-massive-70-000-domain-cybercrime-operation/
- https://github.com/infobloxopen/threat-intelligence/blob/main/cta_indicators/vextrio_cta_20240123_iocs.csv
Kasseika BYOVD
%20concept%2c%20portraying%20the%20potential%20security%20risks%20and%20challenges.%20The%20image.png?width=250&height=250&name=DALL%C2%B7E%202024-01-29%2012.40.40%20-%20A%20darker%2c%20more%20ominous%20interpretation%20of%20the%20Bring%20Your%20Own%20Device%20(BYOD)%20concept%2c%20portraying%20the%20potential%20security%20risks%20and%20challenges.%20The%20image.png) Security researchers at Trend Micro published details on a new ransomware gang known as Kasseika. Discovered in December 2023, this ransomware strain shows many code similarities to BlackMatter, and it is believed that Kasseika is operated by former members of the BlackMatter group.
Security researchers at Trend Micro published details on a new ransomware gang known as Kasseika. Discovered in December 2023, this ransomware strain shows many code similarities to BlackMatter, and it is believed that Kasseika is operated by former members of the BlackMatter group.
One of the more notable techniques of Kasseika is the use of "Bring Your Own Vulnerable Driver," or BYOVD.
Kasseika has been observed abusing a vulnerable driver from TG Soft's VirtIT Agent System, martini.sys (or viragt64.sys).
By abusing vulnerabilities in signed, legitimate software, threat actors can gain high enough privileges on the system to disable security tools and other processes.
Akira, BlackByte, and AvosLocker are other notable ransomware gangs using this technique.
Attack Chain
Kasseika has been observed gaining initial access via phishing emails that gather account credentials.
They then use Windows PsExec to move laterally across the network. PsExec is also used to run a .bat file that checks for the existence of 'Martini.exe', the process required to abuse the vulnerable driver. Once the 'Martini.exe' process has been identified, it is terminated by the batch script, and a vulnerable version of the 'martini.sys' driver is downloaded. The flaws in the vulnerable driver version are then exploited for privilege escalation.
Once this is achieved, the malware terminates 991 processes from a hardcoded list. This list includes various Windows processes, including security tools, as well as many other well-known AV and endpoint security processes.
It should be noted that CrowdStrike’s Falcon Agent is not a part of this list. After this is accomplished, the ransomware encrypts files on the system, and then erases logs of its activity leveraging 'wevutil.exe'.
How To Protect Your Organization
Standard phishing protections will help prevent threat actors such as Kasseika from gaining initial access. User awareness training on how to spot fake login portals is very important. Additionally, phishing-resistant multi-factor authentication (MFA) should be enabled on every user account.
Organizations need to know which remote access tools are allowed on their network, as well as how they are typically used (establish a baseline of normal activity). In the case of Kasseika, PsExec is used for lateral movement. Other ransomware actors use commercial remote access tools such as AnyDesk. Any use of an unauthorized remote access tool, or unusual usage of an authorized remote access tool should be flagged and immediately investigated.
One of the best protections against BYOVD abuse is using a modern EDR tool that has anti-tamper capabilities, such as CrowdStrike. These protections make it extremely difficult to terminate or remove the EDR process without the proper access keys. Additionally, monitoring endpoints for bulk termination of processes can be a strong indicator of a malware infection. See here for a CrowdStrike query to search for the presence of the vulnerable files.
Additional Resources
- https://www.trendmicro.com/en_us/research/24/a/kasseika-ransomware-deploys-byovd-attacks-abuses-psexec-and-expl.html
- https://documents.trendmicro.com/images/TEx/20240122-kasseika-iocsXiHKJpM.txt
- https://www.trendmicro.com/vinfo/us/threat-encyclopedia/malware/Trojan.Win64.PINCAV.A
- https://www.bleepingcomputer.com/news/security/kasseika-ransomware-uses-antivirus-driver-to-kill-other-antiviruses/
Vulnerability Roundup
CVE-2024-0204: Fortra GoAnywhere MFT Authentication Bypass
Fortra released a security bulletin detailing a new critical authentication bypass vulnerability in their GoAnywhere Managed File Transfer (MFT) solution. The vulnerability, CVE-2024-0204, allows for a remote unauthenticated user to create administrative users via the administration portal. Security researchers at Horizon3.ai published details on the vulnerability and exploitation, and proof-of-concept exploit code can be found here.
In early 2023, a high severity 0-day command injection vulnerability in the GoAnywhere MFT product, CVE-2023-0669, was leveraged by the Cl0p ransomware gang to compromise over 130 companies.
CVE-2024-0204 affects the following versions:
- Fortra GoAnywhere MFT 6.x from 6.0.1
- Fortra GoAnywhere MFT 7.x before 7.4.1
Administrators are strongly encouraged to upgrade to version 7.4.1 or higher as soon as possible. If an upgrade is not feasible, a workaround is available. In 'non-container deployments', administrators can delete the InitialAccountSetup.xhtml file located in the install directory and then restart the services. For 'container-deployed' instances, replace the InitialAccountSetup.xhtml file with an empty file and restart.
- https://www.fortra.com/security/advisory/fi-2024-001
- https://platform.socradar.com/app/threatfeed/cve/CVE-2024-0204/details
- https://nvd.nist.gov/vuln/detail/CVE-2024-0204
- https://www.bleepingcomputer.com/news/security/fortra-warns-of-new-critical-goanywhere-mft-auth-bypass-patch-now/
- https://nvd.nist.gov/vuln/detail/CVE-2023-0669
- https://packetwatch.com/resources/threat-intel/cve-2024-0204-fortra-goanywhere-mft-authentication-bypass
CVE-2024-20253: Cisco Unified Communications Manager RCE
Cisco published a security advisory detailing a critical unauthenticated remote code execution vulnerability for their Cisco Unified Communications and Contact Center Solutions products. The vulnerability, CVE-2024-20253, can be exploited by sending a specially crafted message to a listening port on a vulnerable device. Successful exploitation allows the threat actor to execute arbitrary commands on the system with 'web services user' permissions, which can further lead to establishing 'root' access on the system. So far, there has been no evidence of this vulnerability being exploited in the wild.
The following products and versions are affected:
- Packaged Contact Center Enterprise (PCCE) versions 12.0 and earlier, 12.5(1) and 12.5(2)
- Unified Communications Manager (Unified CM) versions 11.5, 12.5(1), and 14.
- Unified Communications Manager IM & Presence Service (Unified CM IM&P) versions 11.5(1), 12.5(1), and 14.
- Unified Contact Center Enterprise (UCCE) versions 12.0 and earlier, 12.5(1), and 12.5(2).
- Unified Contact Center Express (UCCX) versions 12.0 and earlier and 12.5(1).
- Unity Connection versions 11.5(1), 12.5(1), and 14.
- Virtualized Voice Browser (VVB) versions 12.0 and earlier, 12.5(1), and 12.5(2).
Fixed versions and instructions for updating can be found here. Administrators are urged to patch as soon as possible.
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-cucm-rce-bWNzQcUm
- https://platform.socradar.com/app/threatfeed/cve/CVE-2024-20253/details
- https://www.bleepingcomputer.com/news/security/cisco-warns-of-critical-rce-flaw-in-communications-software/
CVE-2024-23897: Critical Vulnerability in Jenkins
A recent security bulletin by Jenkins, a continuous integration/continuous delivery and deployment (CI/CD) automation software company, addresses 9 new security issues, including a critical vulnerability in the built-in command line interface (CLI).
Successful exploitation of this vulnerability, CVE-2024-23897, could allow for a threat actor to read files on the system, and in certain configurations can achieve remote code execution.
A full list of the potential ways the vulnerability can be exploited can be found in the Jenkins security bulletin. Vulnerable versions include Jenkins 2.441 and earlier, LTS 2.426.2 and earlier.
Proof-of-concept exploit code has been observed in the wild.
Administrators are urged to patch to the fixed version, Jenkins 2.442, LTS 2.426.3. If the patch cannot be applied, the vulnerability can be mitigated by disabling access to the CLI.
- https://www.jenkins.io/security/advisory/2024-01-24/
- https://platform.socradar.com/app/threatfeed/cve/CVE-2024-23897/details
- https://nvd.nist.gov/vuln/detail/CVE-2024-23897
- https://github.com/viszsec/CVE-2024-23897
- https://thehackernews.com/2024/01/critical-jenkins-vulnerability-exposes.html
Stay updated with PacketWatch's cybersecurity content by subscribing to our monthly newsletter, delivered to your inbox on the last Tuesday of the month.
PacketWatch publishes this report and other cybersecurity threat intel to the security community for free via our blog. If you want personalized threat intel, contact us today to learn about our enterprise threat intelligence services.
Disclaimer
Kindly be advised that the information contained in this article is presented with no final evaluation and should be considered raw data. The sole purpose of this information is to provide situational awareness based on the currently available knowledge. We recommend exercising caution and conducting further research as necessary before making any decisions based on this information.

